Context
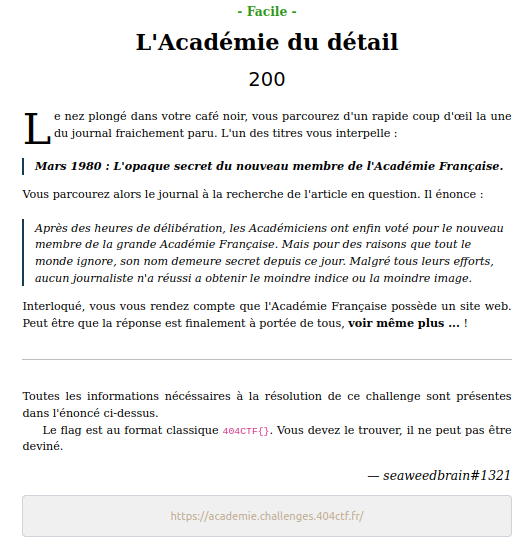
Here is the website main page:

There are 4 endpoints:
- /login -> we can connect as whoever we want as long as it’s not admin
- /logout -> to disconnect
- /home -> just the home page
- /membres to see the members of the academy.
By going to the endpoint /membres we get this page:
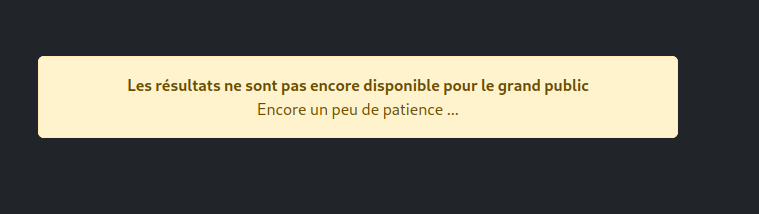
After trying to SQLI the login form, I noticed that we have a JWT token as auth cookie:
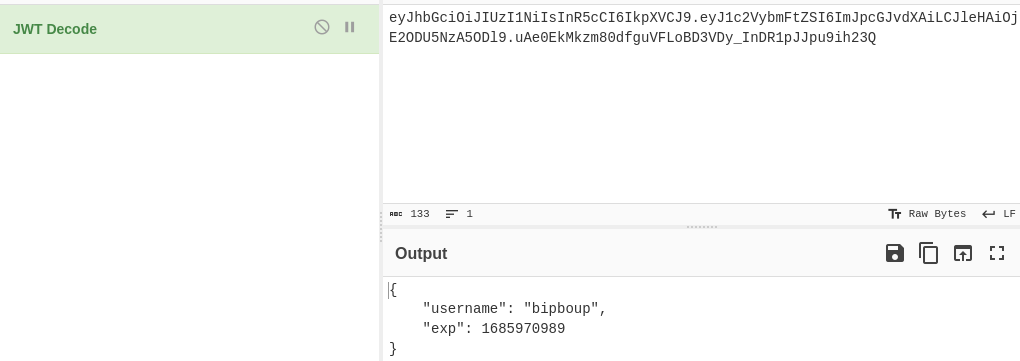
By using Cyberchef, we can decode it (we can also jwt.io or just base64 decode each part):
I tried to change the value of username by “admin” and change the algorithm used for the key by “None”. If the site does not verify that the good algorithm is used, it could validate the token.
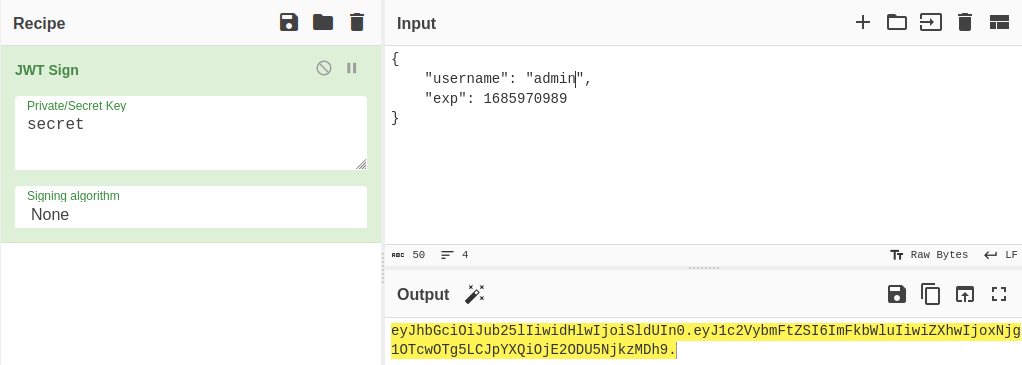
I change the value of the “access-token” cookie by the new value and access the /membres endpoint.
Here we go 😃 !
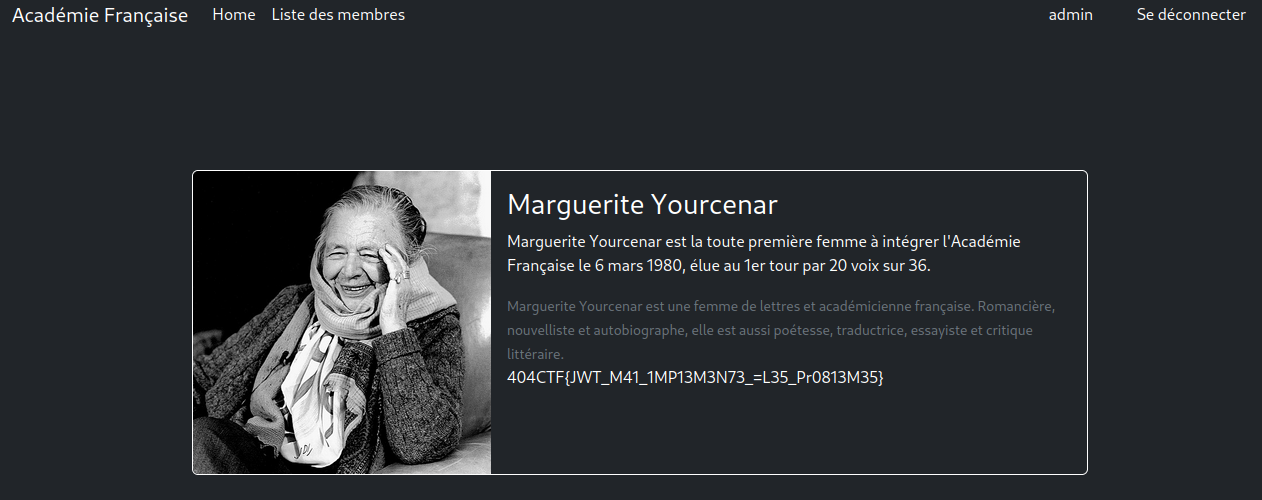
I hope you understood the process. If you want to know more, dig about JWT token vulnerabilities.