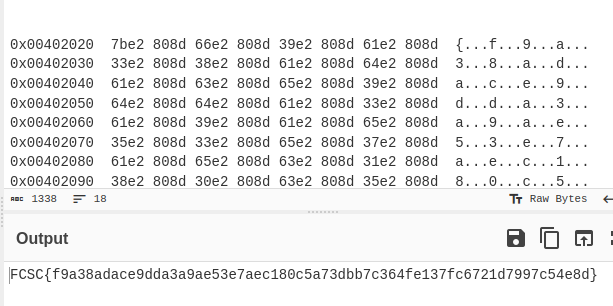
Context
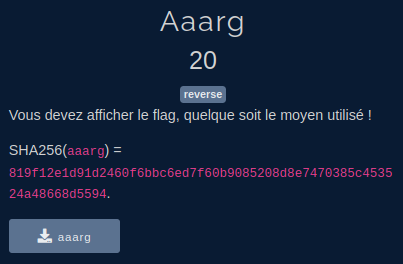
We are given an executable “aaarg”.
Using ghidra, I spoted this:
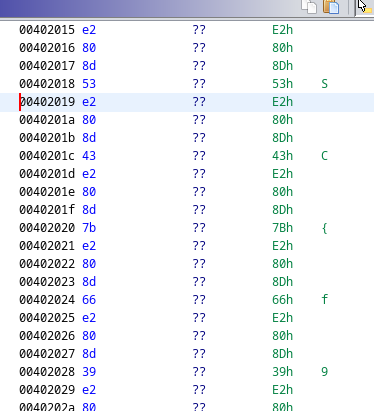
It seems to be the flag.
I opened the executable in radare2 to have a better view of the flag.
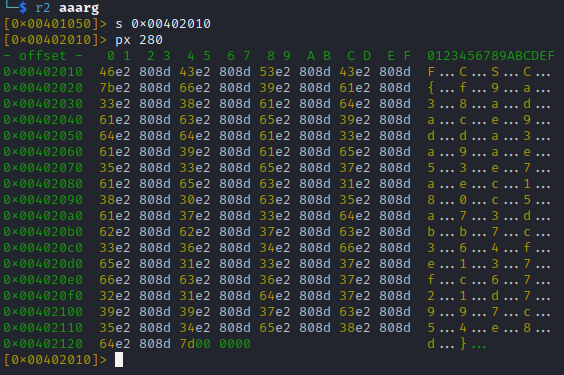
Then I used cyberchef regex and find/replace to assemble the flag:
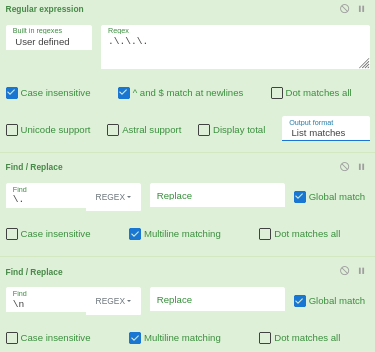
Here is the flag 🥳