Context
We are given a network packet capture, let’s open it with Wireshark.
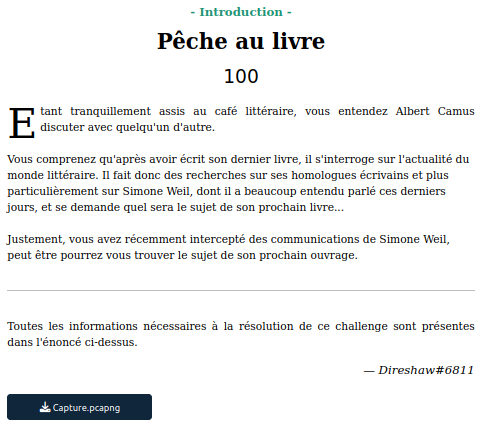
There are 5 TCP conversations on port 80, It must be a web server:
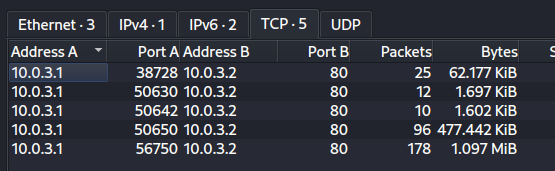
Looking at the Protocol Hierarchy, we can confirm that HTTP is used:
Looking at the conversations (Follow TCP stream), we can see that several images are transfered from the server to the client.
Let’s download them (File > Export Objects > HTTP).
Let’s take a look at them:



We’ve got the flag 🎉 !!
We can use an online OCR (Optical Character Recognition) to retrieve the flag:
404CTF{345Y_W1r35h4rK}
I hope you enjoyed this writeup 😊 !