Context
We have got a wireshark capture named leak.pcapng
I used binwalk on the capture to see if it contains something:
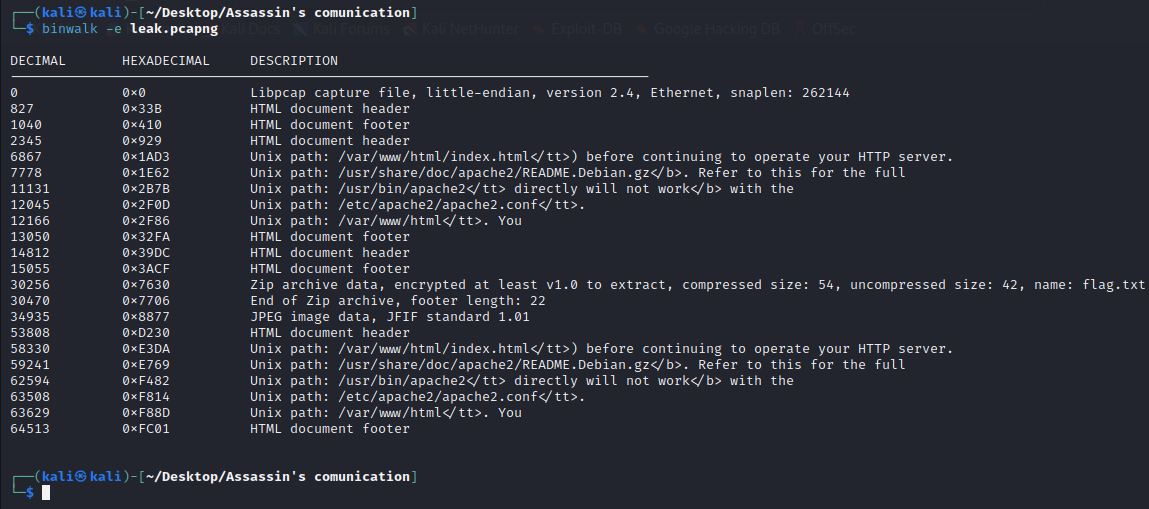
Here is what we have got:
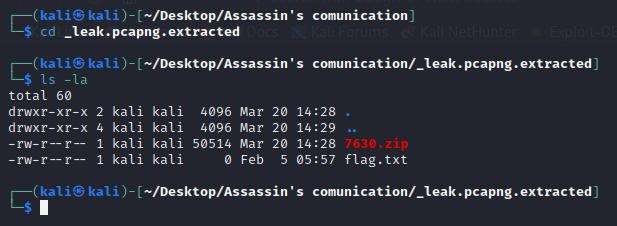
The flag.txt file is empty and the zip file is password protected
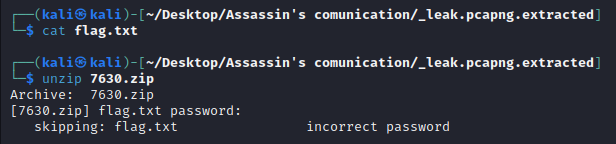
So i decided to crack it !
 Well… I’ve got nothing.
Well… I’ve got nothing.
Let’s take a look at the wireshark capture. Looking at the HTTP conversation, I see that there is an image in the conversation that is in plain text.
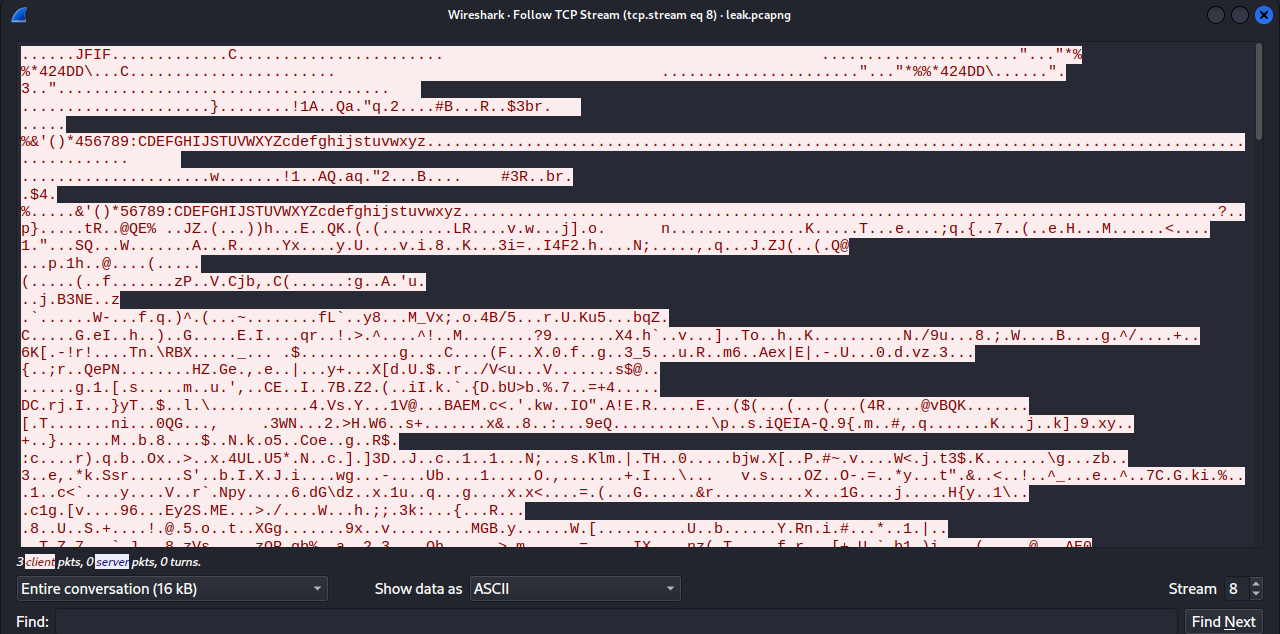
I saved it (put the data in raw first)
And I opened it

Let’s try to run steghide on this image.
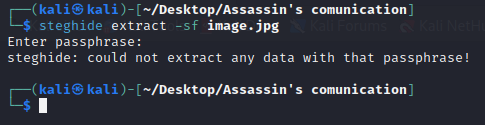
It’s password protected. Let’s try to brute force it with stegseek:
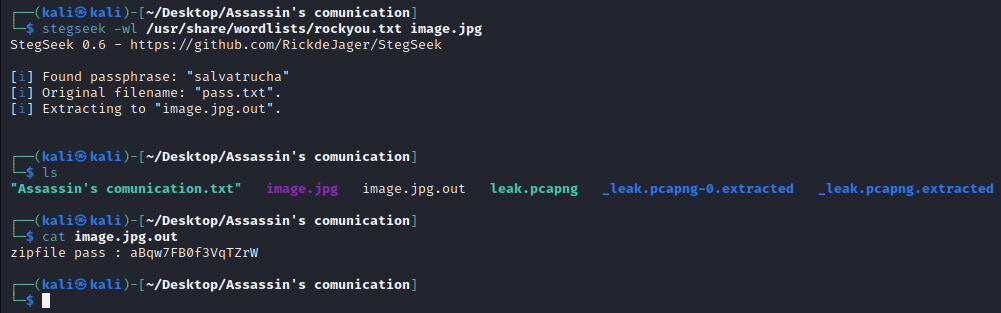
We’ve got the zip password ! (aBqw7FB0f3VqTZrW)
Let’s open the zip file.
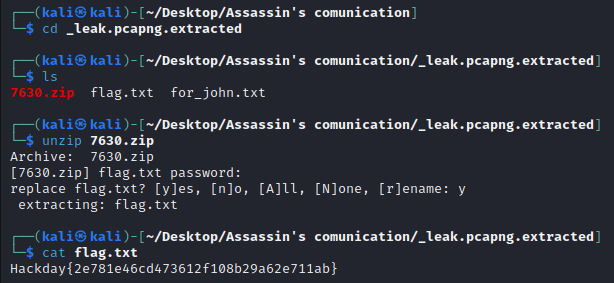
We’ve got the flag, well done !!